Architecture
Warning DoveRunner Mobile App Security team is redesigning On-premise architecture, this document is not up-to-date.
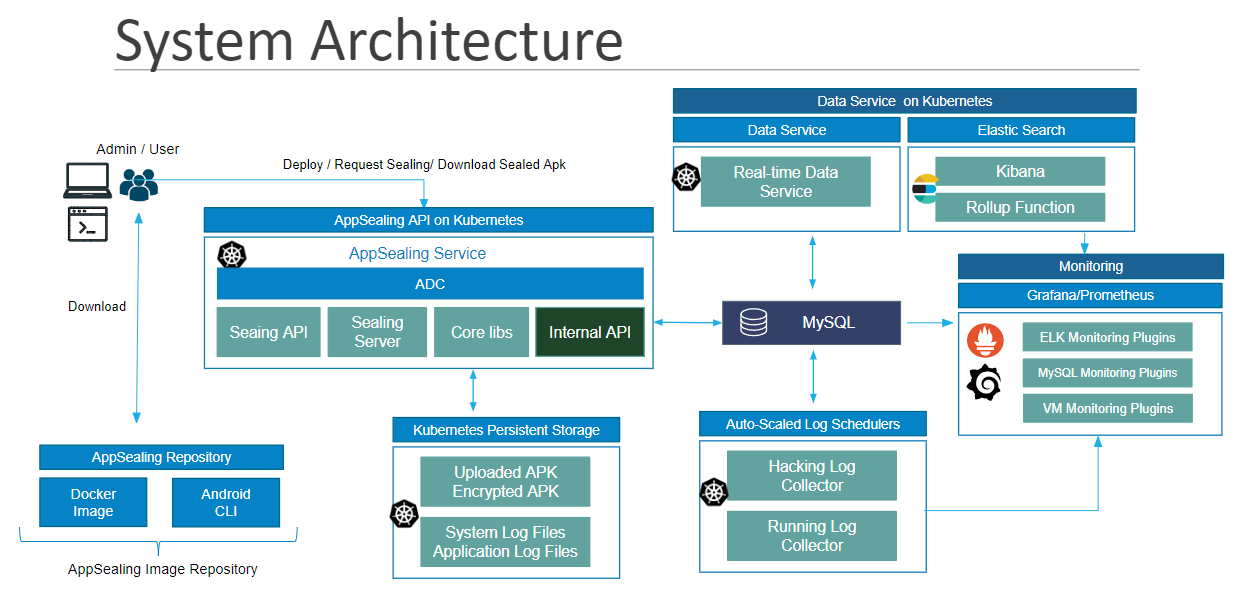
DoveRunner Mobile App Security on-premise version has many modules and requires some external resources like “MySQL Server” and “ElasticSearch Service”. Diagram in Fig.1 shows the interactions between DoveRunner Mobile App Security modules.
Details of DoveRunner Mobile App Security Modules and external resources are listed below.
List of DoveRunner Mobile App Security Internal Modules
Section titled “List of DoveRunner Mobile App Security Internal Modules”| DoveRunner Mobile App Security Module Name | Description |
|---|---|
| ADC (DoveRunner Mobile App Security Developer Console) | Built-in Web Site for managing users, and handling Sealing Requests. |
| API | Restful API for handling Requests from ADC and CLI. |
| Internal API | Handling Interfaces between DoveRunner Mobile App Security modules. |
| Sealing Server | Provides RASP capability to the application files uploaded by the customer. |
| Users can request “Sealing” via ADC/CLI. | |
| Log Scheduler | Collect Reports from mobile devices where DoveRunner Mobile App Security RASP is running. |
| Data Schedulers | Create Daily Statistics and Usage Report |
| Android CLI | Command Line Interface provided by DoveRunner Mobile App Security Service |
List of External Resources
Section titled “List of External Resources”| External Resources | Description |
|---|---|
| MySQL | RDBMS. Version 5.6.10 or higher is required. |
| ElasticSearch Service | ElasticSearch Platform is a data store for collected Reports. Version 7.8.1 or higher is required. |
| Kibana | Kibana is an open-source analytics and visualization platform designed to work with Elasticsearch. |
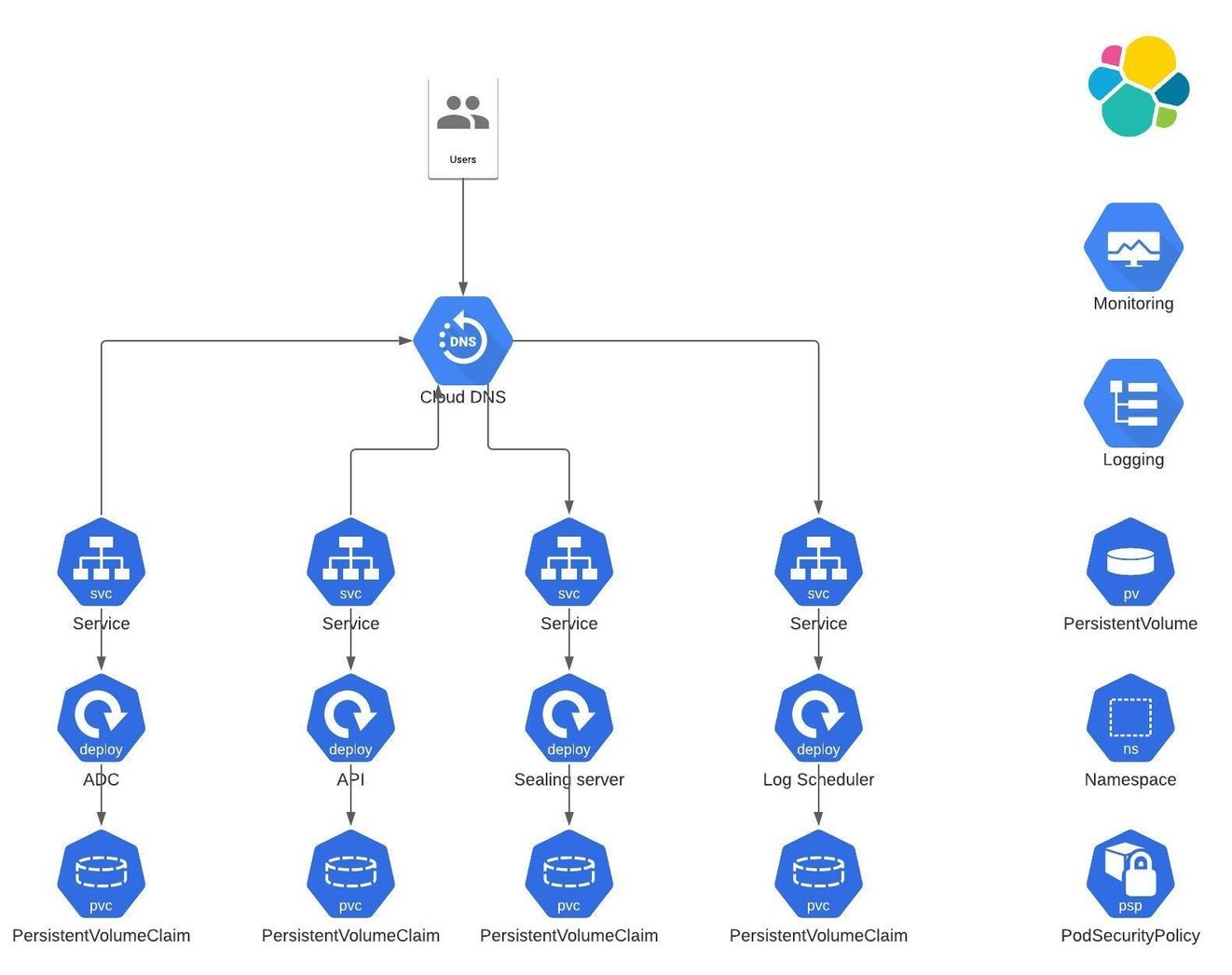
Proposed Kubernetes Architecture
Section titled “Proposed Kubernetes Architecture”This section explains the Kubernetes resources created as part of the deployment.
- Deployment: Deployment means each module, means each container with no of replicas( like minimum and maximum no of containers).
- Service: To access each module/replica set container, we need to create a service and link it with each replica set i.e ClusterIP for internal communication, NodePort for outside/internal communication and LoadBalancer is for outside/internal communication.
- PersistentVolume: PersistentVolume can be anything(e.g. Google Cloud Storage, AWS EBS, EFS or NFS Volume).
- PersistentVolumeClaim: To access PersistentVolume, first we need to create PersistentVolumeClaim and link that Claim with each ReplicaSet.
- ConfigMap: Configmap is the mapping of configuration files, it is used for keeping the configuration variables like version number or some other config variables.
- Secrets: Secrets are used for keeping the secrets like username or password or some other sensitive information.
- ServiceAccount: ServiceAccount is like some user-specified for some task or common user used to perform some operations. We will discuss more in detail during implementation.
- Role: Role is for restricting the user to do some tasks which are not specified for it.
- NameSpace: Namespace is a space where we deploy all the components, It is like a project which contains all the components/modules.